Nowadays, many businesses, no matter how big or small, use digital data transfer more than ever. And with that, security has become a super important part of the application development process. Also, there is no argument that all software companies want to ensure their applications are secure. But nowadays, with so many companies relying on tons of software and cyberattacks happening all the time, it is not always easy to ensure everything is truly safe.
If you don’t take security seriously, it could be a huge problem if there’s a data breach. It can seriously mess up people’s privacy and even ruin your business’s reputation if you’re not careful. So, as a business owner, it is super important to keep security in mind when using customized applications or mobile app development services. Don’t take it lightly!
Luckily, many computer security programs are available these days to help companies and regular folks like you and me ensure we’re using the appropriate software and staying safe.
In this article, we’ll go over what application development security means, the different types of security and risks involved, and some tips/best practices for keeping your application development as secure as possible. Sound good? Let’s dive in!
Table of Contents
What is application development security?
When it comes to IT these days, application development and security go together like peanut butter and jelly. Every step of the development process (the one that goes from idea to finished product) must include some security measures. Application development security means ensuring that all the information used in the project is kept safe and sound and that the final product has no nasty bugs or other problems that could mess things up. It is all about ensuring that our application is top-notch and as secure as possible.
Understanding the Importance of secure application development
In the past, security in application design was an afterthought. Today, from planning through deployment and beyond, it is a growingly important problem for every part of application development. Applications are increasingly being created, utilized, distributed, and patched across networks. As a result, there are more threats than ever that need to be addressed through application security procedures.
Application security, which includes controlling and monitoring application vulnerabilities, is crucial for several reasons. Here are some reasons why this is so important:
- Finding and repairing vulnerabilities lowers risks and hence aids in reducing the overall attack surface of an organization.
- It can help you catch design mistakes before they become bigger problems in the code. This is important because fixing a mistake early on is usually easier and cheaper than fixing it later.
- App flaws are a typical occurrence. Even noncritical vulnerabilities, though not all dangerous, can be compounded and used in attack chains. Keeping flaws and vulnerabilities to a minimum lessens the overall impact of attacks.
- Application security should be approached proactively rather than with reactive measures. By being proactive, defenders can spot and stop attacks earlier, sometimes even before any harm is done.
- Attacks on these assets may increase as businesses shift their data, code, and operational processes into the cloud. Application security measures can lessen the impact of such assaults.
- A secure development process can help stakeholders understand the importance of investing in secure methodologies. They’ll see that it’s important to prioritize security over speed when developing applications and won’t rush developers to release software before it’s ready.
An enterprise may face existential concerns if its application development security is neglected. 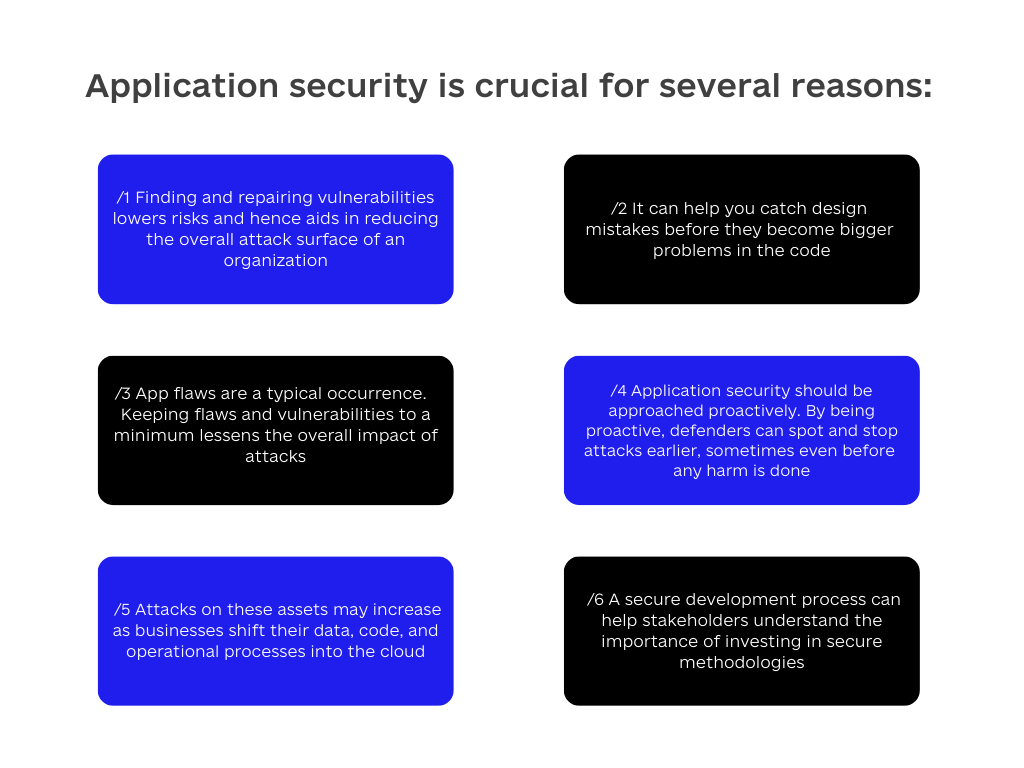
Best Practices for Securing Application Development
You’ll need to develop a strategy, just like with any other procedure, to ensure that your software security measures stay effective and serve your interests. We’ve included a few secure application development best practices below.
- Conducting thorough risk assessments to identify potential vulnerabilities and threats.
When protecting your stuff from attackers, thinking like an attacker is important. That might sound a little weird, but it means putting yourself in their shoes and figuring out where they might try to break in.
So, step one is to create a list of everything you need to protect, including your website, data, applications, or anything else important to you. Next, you must identify the threats and determine how to contain them. Maybe there are certain areas where your security is weaker, or you’re particularly vulnerable to certain types of attacks. Once you identify the threats, you can start building up your defenses.
Another thing to look out for is attack vectors, which are ways attackers might try to get into your system. Maybe they’ll try to exploit a vulnerability in your code or use social engineering to trick you or your users into giving up sensitive information. It is important to identify these attack vectors so that you can block them before they cause any damage.
Of course, having the appropriate measures in place is crucial too. You must ensure you’re using tools like firewalls, antivirus software, and intrusion detection systems to detect and prevent attacks. If you’re unsure whether your current setup is enough, it might be time to look into additional or different tools.
- Follow the principle of least privilege and implement strong authentication and authorization mechanisms.
Giving application users the absolute minimum access to the programs they need to complete their jobs is known as least privilege. Remember how you only need some features when using certain software to complete your work? Well, that’s the whole idea behind least privilege!
You can also implement other strong authentication and authorization mechanisms like two-factor authentication. Doing this makes it way harder for hackers to get into the system and mess things up. It is also good practice to recheck who has access to what, especially when people switch jobs or leave the company altogether. That way, you can be sure that no one has access to anything they shouldn’t.
- Regularly updating and patching all software and systems used in the development process to address known vulnerabilities.
So, you know how sometimes you encounter problems developing an application? It happens to the best of us! But did you know that hackers can take advantage of those issues to target app users? That’s why keeping your software up-to-date and installing the latest patches is very important.
Luckily, there are some great services and tools out there that can help you stay on top of all your software maintenance. They can help you keep track of all your different programs and ensure everything runs smoothly and securely.
- Ensure secure coding practices like input validation, output encoding, and proper error handling.
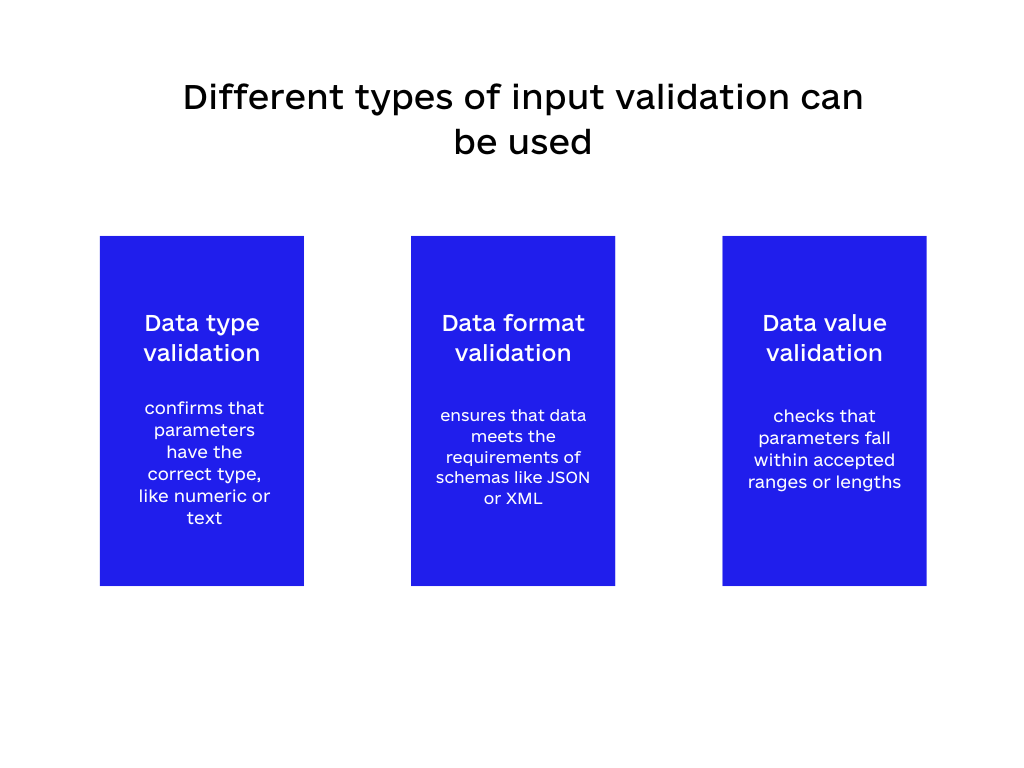
It is generally a good idea to assume that any input you receive is potentially harmful until you confirm it’s not. To make sure only properly structured data goes through an application’s workflow, secure coding practices like proper error handling, output encoding, and input validation are performed. Doing this prevents any corrupted or problematic data from being processed and causing downstream issues.Different types of input validation can be used, such as:
➤Data type validation: confirms that parameters have the correct type, like numeric or text.
➤Data format validation: ensures that data meets the requirements of schemas like JSON or XML.
➤Data value validation: checks that parameters fall within accepted ranges or lengths.
- Implementing encryption techniques for data at rest and in transit, including HTTPS and SSL/TLS protocols.
Encryption is not only the most popular method for securing sensitive data in transit, but it may also be used to secure data “at rest,” such as information kept in databases or other repositories. Information must first be encoded using encryption protocols to be secured against unauthorized access. Although encryption by itself does not shield data transmission from intervention, it obscures the content’s meaning for those without access rights.
Another very effective (and occasionally essential) preventative technique that may be used to protect information is encryption at the service level. HTTPS (SSL/TLS protocols) is typically used for this. In addition to implementing an authentication strategy for entities accessing web services and APIs, you should encrypt the data between those services.
- Conducting regular security audits and incorporating logging and monitoring mechanisms.
Another thing that must be considered is server-level auditing and logging. Fortunately, much of this is integrated into content-serving software programs like IIS (Internet Information Services), making it simple to access in case you need to check various activity-related data.
Logs provide individual responsibility by keeping track of a user’s actions and are frequently the only evidence that suspicious activity is occurring. Activity or audit logging should not require nearly as much setup as error logging because it is typically integrated into the webserver software. Use it to identify unauthorized activity, monitor end-user behavior, and examine application faults missed at the code level.
- Educating and training developers and other stakeholders about best practices and maintaining security awareness.
Pushing a button won’t make software security problems disappear immediately. Employee education is crucial to ensuring software security and reducing software risks.
Set aside one day every three months to examine software security concerns, the significance of the data, and the steps employees may take to protect the organization and themselves. Educating staff members on how to spot warning indications of breaches, phishing scams, etc., is essential.
- Conducting regular security audits and incorporating logging and monitoring mechanisms.
Additional Considerations for Enhanced Security
Because it is important to ensure maximal and secure application development, we can never be too security conscious. Below are additional tips to consider.
- Implementing a robust and secure authentication and authorization system for user access and employing multi-factor authentication (MFA) for added security.
When creating a web application, it is really important to ensure you’re taking steps to keep your users’ accounts safe. One thing you can do is make sure everyone is using strong passwords and that you have a secure way for them to recover their passwords if they forget.
Another good idea is to use multi-factor authentication, meaning users must provide more than one type of information to log in. You can also make users re-authenticate when they try to access sensitive features to ensure it’s them.
When designing your app, try giving users the least access they need to do what they need. Doing this will protect your app from people trying to hack into it.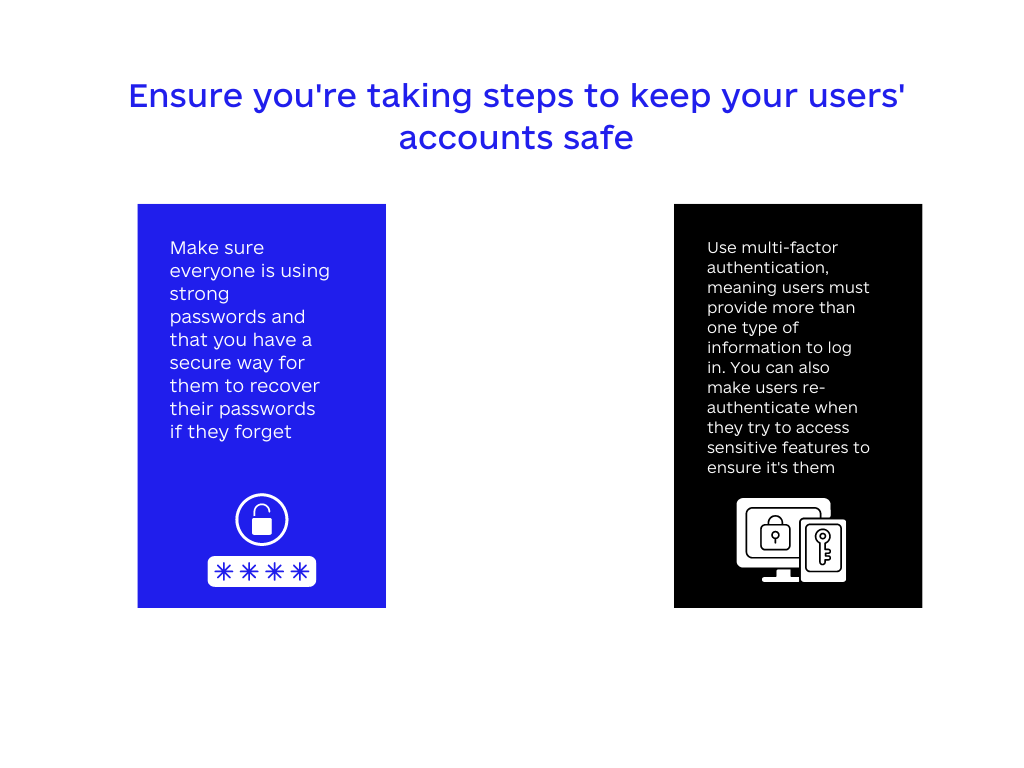
You can also do other things to keep accounts secure, like making passwords expire after a certain time, locking accounts if there are too many login attempts, and using SSL to ensure information is sent securely.
- Regularly review and update access permissions and privileges to ensure only authorized personnel can access sensitive information.
Periodically check and verify that the authorized people have the precise level of access to data and resources and that any unnecessary or outdated permissions are promptly revoked. Doing so can help minimize the risk of unauthorized access and protect sensitive information from potential breaches.
- Implement security measures for third-party libraries, APIs, and other dependencies in application development.
Applications today frequently rely on code constructed using third-party components, many of which are open-source. While DAST/IAST/SAST tests continue to detect flaws in applications that largely rely on third-party libraries, you can save a ton of time and effort by identifying well-known insecure versions of such components utilizing an SCA solution.
Ensure that any third-party libraries, APIs, or other dependencies you’re using are secure by taking steps to prevent potential security vulnerabilities or breaches. To implement security measures, you could start by researching the libraries, APIs, or dependencies you plan to use. Look for any known issues or vulnerabilities, and update them to the latest version that addresses these issues.
- Conduct regular backups of all application data and implement disaster recovery plans.
Breaches will occur even with all due diligence since nothing is 100% secure. A recovery plan for the security of software is essential because of this. How will you behave if something goes wrong? How will you tell when someone is trying to attack you and ensure the damage they cause is minimal? Conducting regular data backups, saving data to the cloud, and implementing disaster recovery plans will mitigate losses from breaches or other incidents.
- Keeping up-to-date with the latest security trends, news, and best practices to stay ahead of emerging threats.
Keeping up-to-date with the latest trends, news, and best practices in application development security is crucial to staying ahead of emerging threats. To do this, you must stay informed about the newest developments in cybersecurity, follow industry blogs and social media accounts, attend training sessions and conferences, and continually learn from experts in the field. By staying informed and up-to-date, you can help ensure your applications and systems are as secure as possible.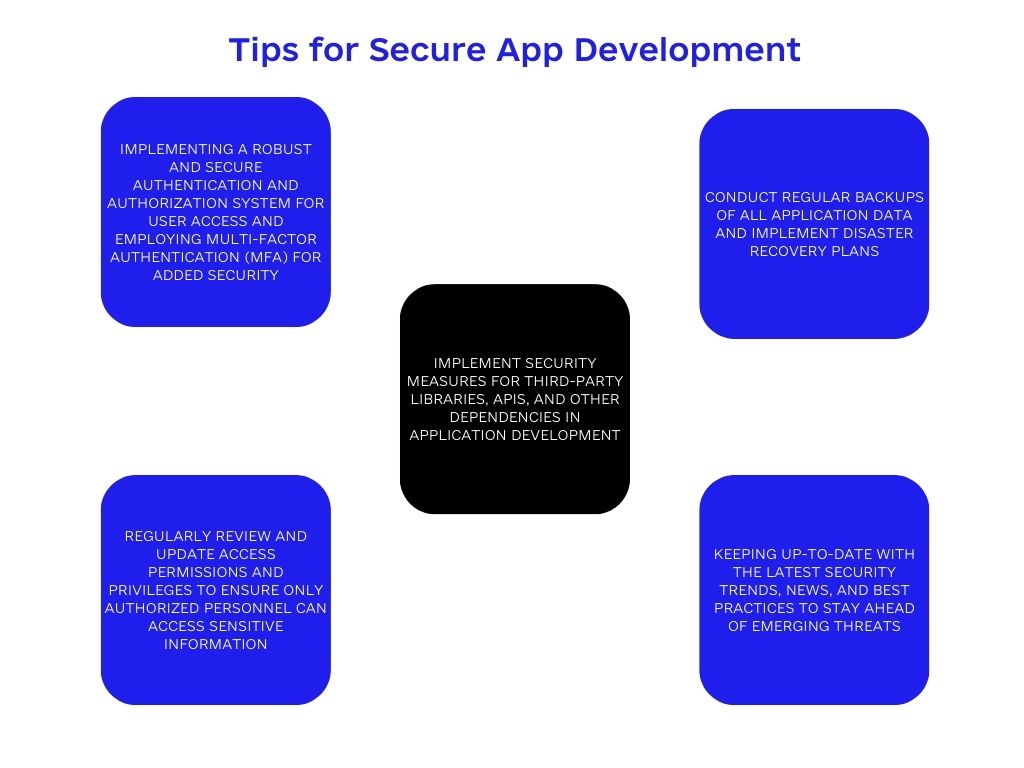
The Bottom Line
Nowadays, we rely on applications for almost everything in business, making us more vulnerable to attacks. While experts undoubtedly have a wide range of perspectives and ideas regarding the best practices for application security, most concur that a few essential factors, as discussed above, should be on any checklist for application security reviews.
As hackers get smarter and new ways of attacking come up, we need to be smart too and change our approach to security. To ensure we are more difficult targets to exploit, we should always strive to be better protected than the competition and make every effort to reduce the number of flaws in our applications.
We can’t expect to stop all attacks, but we can stay ahead of them by gathering information and being prepared. It entails making sure we have enough resources to build an active defense that can detect and respond to any threats that come our way. The app security world is always changing, so we must adapt our strategy to keep up with it.
If you want to keep your applications safe, get in touch with Code&Care.
















Popular
Latest